A PDF version of the following article can be accessed here.
Introduction
Care England attended a Leadership Through Data training session on 17 January 2023 titled ‘All You Need To Know: Caldicott Guardian’. This session provided an overview of a Caldicott Guardian (CG) ‘s role within an organisation and the responsibility they serve in information governance.
This page outlines an overview of what a Caldicott Guardian is, their responsibilities and why social care organisations should consider hiring one or ensure their duties are facilitated by staff.
This brief is broken down into the following content:
- Information Governance and Data Protection
- What is a data breach?
- What is a Caldicott Guardian?
- What are the Caldicott Principles?
- Caldicott Guardian vs Other IG Roles
- Caldicott Guardian within a Social Care Organisation
- What Good Looks Like
- Considerations for Adult Social Care Providers
Information Governance and Data Protection
Whilst information governance and data protection are often viewed as a part of digital transformation and rely on the need for digital tools, this is far from the truth. IG has continued to play a key role within an organisation’s integral structure since business records began. Pre-digital technology and particularly pre-internet and the world-wide-web, IG was better practised amongst organisations and institutions. In 1998 for example, there were better data protection systems in place due to the majority of records being paper-based still. Whilst paper-based records have significant faults, one benefit and, as such, provide better data protection, is that there would be individuals whose sole role was to archive documents, providing limited access to the data and ensuring an effective filing process.
Due to the digitisation of paper-based records to online, there became greater access to information and records. As such, filing and arching became more sloppy and standards began to slip. As business and society become more digitised, information governance and data protection must be maintained. This is particularly the case within a social care setting, where there are huge amounts of sensitive confidential information about individuals in receiving care and staff.
As with many workstreams, information governance crosses over several different areas of an organisation (as shown below).
Social care organisations should consider where their financial, information and service governance cross over and who oversees such duties. It is important that staff within an organisation know who is responsible for such converges and ensure there are correct checks and balances to ensure the right procedures are being followed and the right individuals are involved.
Organisations should also factor in the National Data Guardian’s Leadership Obligations and Data Security Standards. Digital Social Care has provided a page with these standards (access here). The standards come under three leadership obligations:
People
Ensure staff are equipped to handle information respectfully and safely, according to the Caldicott Principles.
Data Security Standard 1. All staff ensure that personal confidential data is handled, stored and transmitted securely, whether in electronic or paper form. Personal confidential data is only shared for lawful and appropriate purposes.
Data Security Standard 2. All staff understand their responsibilities under the National Data Guardian’s Data Security Standards, including their obligation to handle information responsibly and their personal accountability for deliberate or avoidable breaches.
Data Security Standard 3. All staff complete appropriate annual data security training and pass a mandatory test, provided through the revised Information Governance Toolkit.
Process
Ensure the organisation proactively prevents data security breaches and responds appropriately to incidents or near misses.
Data Security Standard 4. Personal confidential data is only accessible to staff who need it for their current role and access is removed as soon as it is no longer required. All access to personal confidential data on IT systems can be attributed to individuals.
Data Security Standard 5. Processes are reviewed at least annually to identify and improve processes which have caused breaches or near misses, or that force staff to use workarounds which compromise data security.
Data Security Standard 6. Cyber-attacks against services are identified and resisted and CareCERT security advice is responded to. Action is taken immediately following a data breach or a near miss, with a report made to senior management within 12 hours of detection.
Data Security Standard 7. A continuity plan is in place to respond to threats to data security, including significant data breaches or near misses, and it is tested once a year as a minimum, with a report to senior management.
Technology
Ensure technology is secure and up-to-date.
Data Security Standard 8. No unsupported operating systems, software or internet browsers are used within the IT estate.
Data Security Standard 9. A strategy is in place for protecting IT systems from cyber threats which are based on a proven cyber security framework such as Cyber Essentials. This is reviewed at least annually.
Data Security Standard 10. IT suppliers are held accountable via contracts for protecting the personal confidential data they process and meeting the National Data Guardian’s Data Security Standards.
What is a Data Breach?
Data breaches cover many malicious/unmalicious events that impact an organisation’s data storage. In the context of adult social care, providers must be aware of what a personal data breach is. The Information Commissioner’s Office (ICO), defines a personal data breach as:
“A personal data breach can be broadly defined as a security incident that has affected the confidentiality, integrity or availability of personal data.”
Therefore, all staff within an adult social care organisation must understand what counts as personal data. ICO defines personal data as information related to an identified or identifiable individual. This could be an array of inputs including but not limited to:
- Name
- Identifiable number
- IP address
- Cookie identifier
Under the Data Protection Act 2018, data is broken down into four categories
Anonymisation means that individuals are not identifiable and cannot be re-identified by any means reasonably likely to be used (ie, the risk of re-identification is sufficiently remote). Anonymous information is not personal data and data protection law does not apply.
Pseudonymisation can reduce the risks to individuals. It can also help you meet your data protection obligations, including data protection by design and security. However, it does not change the status of the data as personal data when you process it in this way
Personal data means any information relating to an identified or identifiable natural person (‘data subject’); an identifiable natural person is one who can be identified, directly or indirectly
Special category data is personal data that needs more protection because it is sensitive. Examples include: religion or other beliefs; sex life; trade union; race/ethnicity; biometrics used to ID; political opinion; physical and/or mental health condition
If there is a personal data breach within the organisation, Data Processors and Data Controllers must follow the below process, within 72 hours. A Data Processor (DP) is a computer or person that carries out operations on data to retrieve, transform, or classify information. A Data Controller (DC) is an individual who makes decisions about processing activities. They exercise overall control of the personal data being processed and are ultimately in charge of and responsible for the processing.
Within an adult social care setting, many individuals cannot understand the situation of a personal data breach. Therefore, providers should have the correct contacts (families etc.,) in place to whom they should be reaching out if such an event occurs.
All staff within an organisation must understand the above process. If a data breach is left unaddressed, it can lead to criminal action. If criminal action is taken, it is unclear who would be liable, the organisation or the staff member that caused the breach (or failed to follow the due process). There are cases that support both sides of the argument as to who is responsible for the breach. Of course, it is impossible to prevent a data breach, however, it is all about development vs protection and how they reduce the likelihood of a breach. To reduce the chances of a personal data breach, providers must ensure that staff are aware of correct procedures and there are regular retraining programmes in place.
What is a Caldicott Guardian?
Information governance and data protection should be understood and practised by all within a social care organisation. The organisation is responsible for ensuring that good data protection and process is heard and understood by all staff. This includes auxiliary and ancillary staff. The provider has a responsibility to ensure that data protection is practiced by all employees that are hired for a service. If the provider is a multi-site organisation (i.e., has a head office and several social care settings), all sites should be aware of what is expected of them and the staff. A Caldicott Guardian can help facilitate and keep in check an organisation’s process for data protection and ensure that ethical data handling is maintained.
A Caldicott Guardian (CG) is a senior person within a health or social care organisation who makes sure that the personal information about those who use its services is used legally, ethically, and appropriately, and that confidentiality is maintained. Caldicott Guardians should provide leadership and informed guidance on complex confidentiality and information sharing matters.
The Caldicott Guardian should play a key role in ensuring that their organisation satisfies the highest practical standards for handling person-identifiable information. Their main concern is information relating to patients, service users and their care, but the need for confidentiality extends to other individuals, including their relatives, staff and others. Organisations typically store, manage, and share personal information relating to staff, and the same standards should be applied to this as to the confidentiality of patient information.
As it stands according to the Government, all NHS organisations and local authorities that provide social services must have a Caldicott Guardian. Currently, social care organisations do not require a CG within their organisation, however, by 30 June 2023 all health and social care organisations handling confidential information will be required to have a CG within their organisation. This decision follows a public consultation by the National Data Guardian (NDG), which stated the need for Caldicott Guardians across the wider health and social care sector. Digital Social Care will be providing supporting material for providers to help ensure that they are compliant.
The following terms are part of the vocabulary of ethical data handling and wider information governance and should be at the back of a Caldicott Guardian’s mind.
What are the Caldicott Principles?
Eight principles apply to the use of confidential information within health and social care organisations, when such information is shared with other organisations, and when conducting work that involves wider information governance (IG).
- Justify the purpose(s) for using confidential information
Every proposed use or transfer of confidential information should be clearly defined, scrutinised, and documented, with continuing uses regularly reviewed, by an appropriate guardian(s).[1]
- Use confidential information only when it is necessary
Confidential information should not be included unless it is necessary for the specified purpose(s) for which the information is used or accessed. The need to identify individuals should be considered at each stage of satisfying the purpose(s) and alternatives used where possible
- Use the minimum necessary confidential information
Where the use of confidential information is considered to be necessary, each item of information must be justified so that the minimum amount of confidential information is included as necessary for a given function.
- Access to confidential information should be on a strictly need-to-know basis
Only those who need access to confidential data should have access to it, and then only to the items that they need to see. This may mean introducing access controls or splitting information flows where one flow is used for several purposes.
- Everyone with access to confidential information should be aware of their responsibilities
Action should be taken to ensure that all those handling confidential information understand their responsibilities and obligations to respect the confidentiality of patients and service users.
- Comply with the law
Every use of confidential information must be lawful. All those handling confidential information are responsible for ensuring that their use of and access to that information complies with legal requirements set out in statute and under common law.
- The duty to share information for individual care is as important as the duty to protect patient confidentiality
Health and social care professionals should have the confidence to share confidential information in the best interests of the patients and service users within the framework set out by these principles. They should be supported by the policies of their employers, regulators and professional bodies.
- Inform patients and service users about how their confidential information is used
A range of steps should be taken to ensure no surprises for patients and service users, so that they can have clear expectations about how and why their confidential information is used, and what choices they have about this. These steps will vary depending on the use: as a minimum, this should include providing accessible, relevant and appropriate information – in some cases, greater engagement will be required.
Caldicott Guardian vs Other IG Roles
Within the world of information governance, there are varying roles that seek to facilitate different functions that impact an organisation’s strategy towards data and overall information governance. It can be difficult to understand the differences between these roles, why they are different, and the importance (where possible), of having different individuals facilitate these duties.
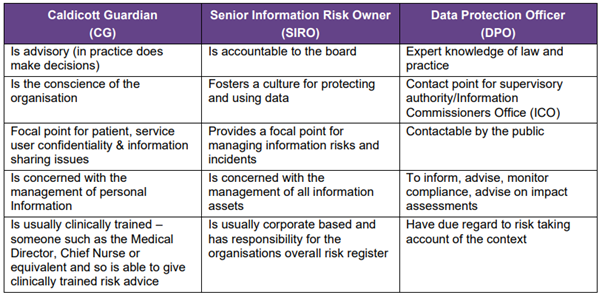
The below table summarises the different roles and duties of three information governance roles. Caldicott Guardian (CG), Senior Information Risk Owner (SIRO) and Data Protection Officer (DPO).
As the table demonstrates, each similar role has unique responsibilities that differ from the other. Outside of the roles highlighted within the table, there are also Information Governance Leads (IG Leads). These individuals are responsible for co-ordinating IG, monitoring access to personal data and ensuring compliance with Data Protection Subjects Requests (SARs).
Caldicott Guardian within a Social Care Organisation
Many adult social care organisations operate at an SME level and therefore it could be difficult for an organisation to employ an individual to facilitate the responsibilities of a Caldicott Guardian. A company can have a singular CG or multiple within their organisation. Where one individual cannot facilitate every duty a CG holds (in an SME for example), their duties can be shared across multiple individuals. However, it should be clear who is the senior staff member who is ultimately accountable for overseeing the CG duties. An organisation may feel that a DPO or IG Lead could take on the responsibilities of a CG (if they employ such a role), however, there are issues with this approach.
A Caldicott Guardian is supposed to operate as independently as possible to ensure that their focus is on ensuring data is handled ethically within their organisation. CG duties may often contradict that of a DPO or IG Lead so a social care organisation has to consider who will facilitate what duties within their organisation. Therefore, when a care provider cannot facilitate an individual to the role of Caldicott Guardian, there must be a clear outline/structure of who within the organisation is accountable for CG duties, shared amongst senior figures for example. Whatever the provider decides is the most suitable direction, it needs to be clearly communicated to each member of the organisation and included in training new staff and retraining of current employees.
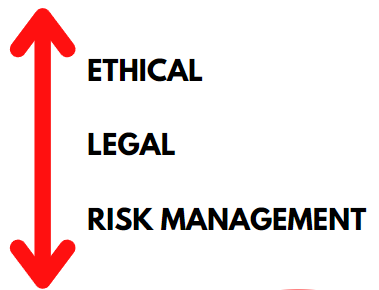
There are three ways to look at information governance and the handling of confidential information:
Ethical: The moral approach to data handling that serves to not abuse/exploit individuals’ data. Ethical data handling falls on whether someone’s data should or shouldn’t be used and whether it will positively affect a said individual.
Legal: What an organisation must lawfully practice when processing/handling data. This does not necessarily mean the bare minimum, however, it removes the morality from decision making. Looking at data governance through a legal framework usually prioritises outcomes for the organisation rather than the individual.
Risk Management: What can a company get away with? Although not necessarily illegal, actions may lead to significant backlash. How long will it be before back practice leads to being caught, or some form of a data breach?
Therefore, a CG must consider where their organisation falls within these three categories when considering their approach to handling confidential data and wider information governance. Quarterly reviews of IG practice within an organisation will help establish and mitigate any occurring or rising factors that could impact IG or lead to a data breach. These reviews would be conducted by the CG or the individual responsible for their duties.
Specific duties of a CG in an adult social care organisation may involve; ensuring accurate data protection is maintained; updating a Caldicott Decision Log (please see below); ensuring an effective and secure filing system is maintained. A decision log could help ensure that information governance is at the forefront of discussions when planning new projects/workstreams that use confidential and/or sensitive information. It will demonstrate the information governance processes/decisions that have occurred and any issues/breaches that have resulted. Keeping a decision log will also help identify any Data Protection Impact Assessment (DPIA). A DPIA describes a process designed to identify risks arising out of the processing of personal data and to minimise these risks as far and as early as possible.
The Digital Social Care website hosts pages and support for care providers to understand what training is out there and how they can better inform staff about best practice.
The CQC also offers support and advice on what healthcare organisations should be facilitating in regard to data protection. Whilst the Safe Care Safe Data review focused on patient data with the NHS, the outcomes and recommendations can be transferred to adult social care settings:
- Leadership
The leadership of every organisation should demonstrate clear ownership and responsibility for data security, just as it does for clinical and financial management and accountability.
- Information, tools and training
All staff should be provided with the right information, tools, training and support to allow them to do their jobs effectively while still being able to meet their responsibilities for handling and sharing data safely.
- IT systems
IT systems and all data security protocols should be designed around the needs of patient care and frontline staff to remove the need for workarounds, which in turn introduce risks into the system.
- Outdated technology
Computer hardware and software that can no longer be supported should be replaced as a matter of urgency.
- Audit and validation
Arrangements for internal data security audit and external validation should be reviewed and strengthened to a level similar to those assuring financial integrity and accountability.
- CQC assessment
Assessment framework and inspection approach to include assurance that appropriate validation against the new data security standards have been carried out, and make sure inspectors are appropriately trained.
These six recommendations echo not only the Caldicott Guardian principles but wider data and digital standards that are seen across different regulators and stakeholders.
As highlighted already, due to the capacity of certain social care organisations, it could be difficult for providers to facilitate the roles of Caldicott Guardians to specific individuals. Providers should therefore consider developing employees into Digital Champions. A Digital Champion supports understanding digital technologies and their confidence and motivation to use them. They can provide an important tool to help improve the digital literacy of our workforce and, therefore, the overall quality of care received by individuals.
Health Education England (HEE) has developed the Adult social care digital champions toolkit following extensive study in other care settings. You can find out more about the role of a digital champion here.
What Good Looks Like
What does good look like (WGLL)? It can be hard to define this term within data protection, ethical handling and wider information governance as it is a forever evolving space. The further society and business digitise, the more complex governance becomes, resulting in organisations requiring to be more thorough. Therefore, what good looks like is a continual improvement cycle that is under constant review and at the forefront of every project/decision. It is about understanding the data within an organisation and the potential risks that come with it.
Data leads, particularly a Caldicott Guardian, must consider whether data is being abused/exploited within their organisation. Rather than looking at data handling as privacy vs functionality, a Caldicott Guardian should consider these processes and complement one another within workstreams and the handling of data.
The diagram below is useful to refer to when considering using confidential information and planning an exercise involving data/data governance.
Plan: Looking holistically at an issue and acting with foresight allows an organisation to strategically consider all positive outcomes, both positive and negative.
Do: Facilitate the task at hand as prescribed by the plan.
Check: Is input meeting output?
Act: Make changes accordingly to resolve errors.
REPEAT
Maintaining a coherent level of thinking that recycles the above process will help meet an organisation’s long-term strategic outputs which involves data processes, and provide a better steer in effectively utilising data. Whilst data/information governance may be viewed as a blocker to innovative initiatives, this is a myth. Having a strong governance and process structure in place allows an organisation to effectively plan with foresight and have strategic oversight of any mitigating risks that may arise from an exercise using data.
DHSC recently published Care data matters: a roadmap for better data for adult social care, a draft document that sets out the government’s roadmap for transforming adult social care data in England and seeks views on the data needed to commission, deliver and oversee care and support.
Part of this roadmap looks to address WGLL in adult social care data collection, this is set to be published in Spring 2023 and will closer align NHSE and social care data collection and handling.
Considerations for Adult Social Care Providers
Adult social care providers should consider the following factors and questions when thinking about their organisation’s data and information governance.
- Who is responsible for data governance at a senior level within the organisation? Is it clear to all staff?
- If the organisation has a board, who reports to the board about the organisation’s data governance?
- Providing clear do’s and do not’s when handling data.
- Would the organisation be prudent to facilitate a Caldicott Guardian decision log?
- Consider regular digital/information governance training in place for all staff.
- Maintenance of hard/software. Providers should consider reviewing and updating their technology tools on a regular basis.
- Preventing personal devices from being used in social care settings as work devices.
- Maintaining an organised filing system that mirrors a paper-based archive is followed by each individual within the organisation.
- Keep a record of processing activities (ROPA) to ensure a comprehensive record of processing activities, ultimately comprised of everything accounted for by listed exercises.
- Keep a record of data records to ensure that there are thorough and robust archiving is in place.
For further discussion please contact:
Louis Holmes
Policy Manager
Care England
lholmes@careengland.org.uk
[1] A company can have a singular CG or multiple within their organisation. Where one individual cannot facilitate every duty a CG holds (in an SME for example), their duties can be shared across multiple individuals. However, it should be clear who is the senior staff member who is ultimately accountable for overseeing the CG duties.









Comments
Login/Register to leave a comment